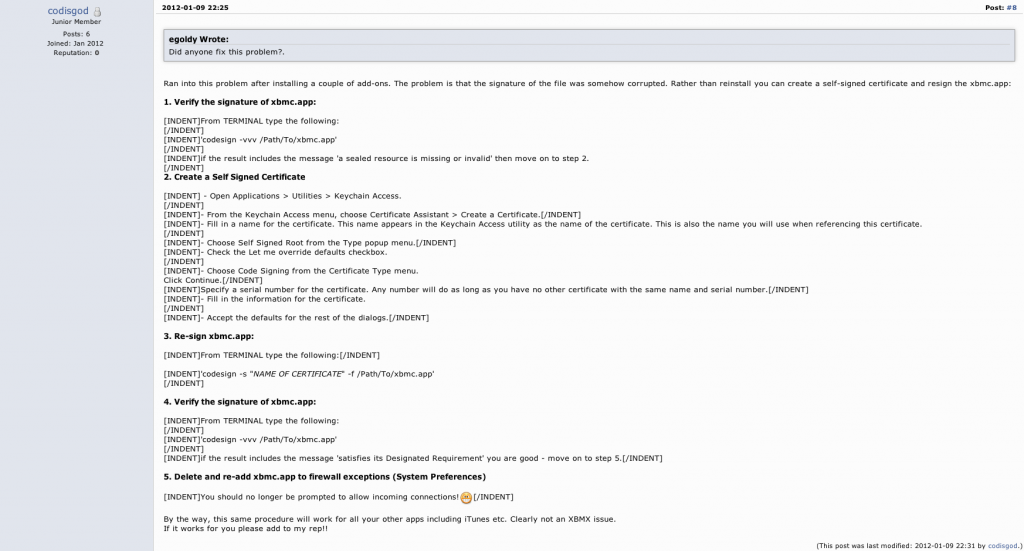
I installed XBMC on my Mac OS X Lion and every time I open up the program, a firewall permission dialog pops up. It didn’t help even if I added the XBMC in my firewall configurations. Popups still show up. This link solves the problem neatly — You can generate a certificate and sign the program by yourself. After that the frustrating dialog should appear only once (at most). In case the link becomes invalid, here’s a screenshot of the instructions. Click to see the large picture.
Leave a CommentTag: Security
My friends and I am working on a hobby project and we need a Git server, so I set up one on my MacBook Pro. We access the repository via SSH. However when I checked the ssh log I found someone trying to get ssh access to my machine by guessing usernames. The log looks as follows:
Jun 29 21:06:52 doh1 sshd[19400]: Invalid user postgres from 190.181.132.70 Jun 29 21:06:52 doh1 sshd[19401]: input_userauth_request: invalid user postgres Jun 29 21:06:52 doh1 sshd[19401]: Received disconnect from 190.181.132.70: 11: Bye Bye Jun 29 21:06:54 doh1 sshd[19402]: reverse mapping checking getaddrinfo for wimax132-70.yota.com.ni [190.181.132.70] failed - POSSIBLE BREAK-IN ATTEMPT! Jun 29 21:06:54 doh1 sshd[19403]: Received disconnect from 190.181.132.70: 11: Bye Bye Jun 29 21:06:55 doh1 sshd[19405]: reverse mapping checking getaddrinfo for wimax132-70.yota.com.ni [190.181.132.70] failed - POSSIBLE BREAK-IN ATTEMPT! Jun 29 21:06:55 doh1 sshd[19405]: Invalid user backup from 190.181.132.70 Jun 29 21:06:55 doh1 sshd[19406]: input_userauth_request: invalid user backup Jun 29 21:06:56 doh1 sshd[19406]: Received disconnect from 190.181.132.70: 11: Bye Bye Jun 29 21:06:57 doh1 sshd[19407]: reverse mapping checking getaddrinfo for wimax132-70.yota.com.ni [190.181.132.70] failed - POSSIBLE BREAK-IN ATTEMPT!
I first tried to use DenyHosts, however, there are still attempts from other IP addresses. Since there are three of us accessing the repository, I configured the hosts.allow and hosts.deny manually: deny all hosts other than the IP addresses I trust.
hosts.deny:
~$ cat /etc/hosts.deny sshd: ALL
hosts.allow:
~$ cat /etc/hosts.allow sshd: [The IP addresses you allow to connect via SSH] ALL: localhost
Now the log file should be quite…
Leave a CommentI wrote a paper on privacy control in social networking sites. You can find the full paper at http://www.cse.hut.fi/en/publications/B/11/papers/li.pdf. Here’s the abstract:
As social networking services become increasingly popular, more and more attacks against users’ private information are reported. As a result, privacy protection becomes an important concern among users. Previous research has produced many different approaches to deal with privacy control in different social networking sites. In this paper, we make a survey on different approaches proposed to tackle the privacy issue in social networking sites. In particular, we put current approaches into three general categories, i.e. approaches addressing end users’ active participation, security automation based on machine learning algorithms, and privacy preserving by using a decentralized architecture for social networkingservices. Then we introduce and analyze some of the approaches in each category. Finally, we give some suggestions that may help privacy control in online social networks.
Leave a CommentIn this project, we explored the performance of the popular hash function MD5 — Message Digest Algorithm Version 5. Firstly we introduce the algorithm in detail. Then we check the algorithm’s complexity in two aspects: computational and space complexity. Furthermore we check the security aspects of MD5: whether it is feasible to find collision it using brute force, birthday attack, and cryptanalysis. Available cryptanalysis methods are introduced so that we can find out why MD5 is not considered secure any more.
The computational complexity of MD5 can be seen from the following diagram:

The bash script used to generate the above diagram is as follows:
#!/bin/sh
# Date: Nov. 28th, 2009
# Usage: ./timemd5.sh Directory_Name
USAGE='Usage: ./timemd5.sh Directory_Name'
if [ $# != 1 ]
then
echo $USAGE
exit
fi
if [ -d $1 ]
then
DICTORY=$1
else
echo $USAGE
exit
fi
# Create a statics file
DATE=`date +%Y%m%d%H%M%S%N`
STATICS="$HOME/statics.$DATE"
if [ ! -e "$STATICS"]
then
touch "$STATICS"
fi
cat /dev/null >$STATICS
cd $DICTORY
# For each file in the directory,
# compute its MD5 value with 'md5sum'.
# And record the file size and the time
# it takes to compute its MD5 hash.
find $PWD -iname "*" |\
while read i
do
if [ -f "$i" ]
then
echo "Calculating MD5 for: $i"
SIZE=`du -m "$i" |cut -f1`
(time -f "%e" -o /tmp/time md5sum \
"$i")1> /dev/null
TIME=`cat /tmp/time`
echo "$SIZE\t\t$TIME" >>$STATICS
fi
done
rm /tmp/time
echo "Size\t\tTime"
cat $STATICS
# Draw a more straightforward graph
# using 'gnuplot'
cd $HOME
GNUPLOTFILE="plot"
echo "set terminal postscript eps 22" \
>$GNUPLOTFILE
echo "set output \"graph.eps\"" \
>>$GNUPLOTFILE
echo "set key left top Left" \
>>$GNUPLOTFILE
echo "setxlabel \"File Size (M)\"" \
>>$GNUPLOTFILE
echo "set ylabel \"Processing Time (s)\"" \
>>$GNUPLOTFILE
echo "plot [0:1500][0:50] \""$STATICS"\" \
with points ps 1 pt 7 title \"\"" \
>>$GNUPLOTFILE
gnuplot <$GNUPLOTFILE
evince graph.eps&
#rm $GNUPLOTFILE
#rm $STATICS
echo "Task done!"
exit
One Comment